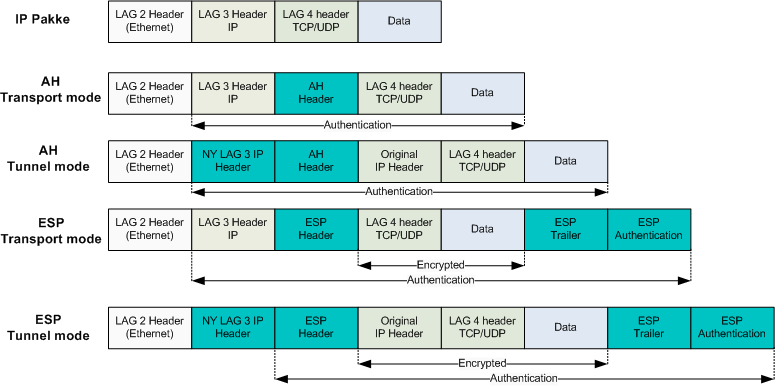
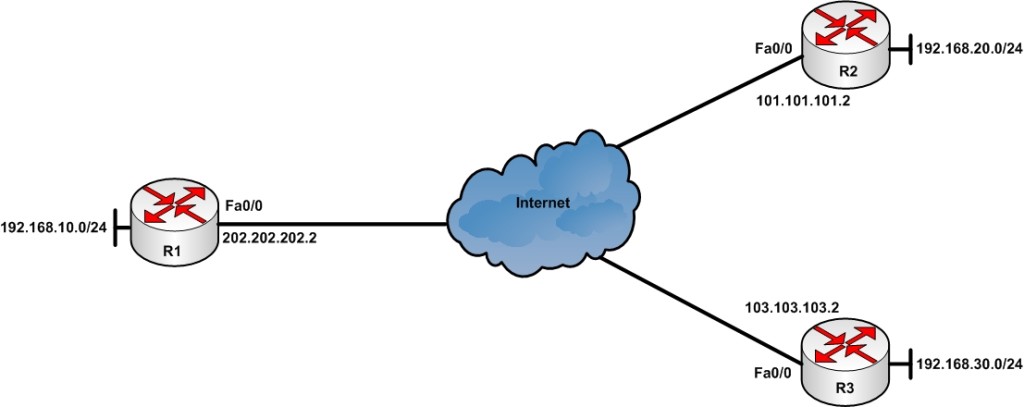
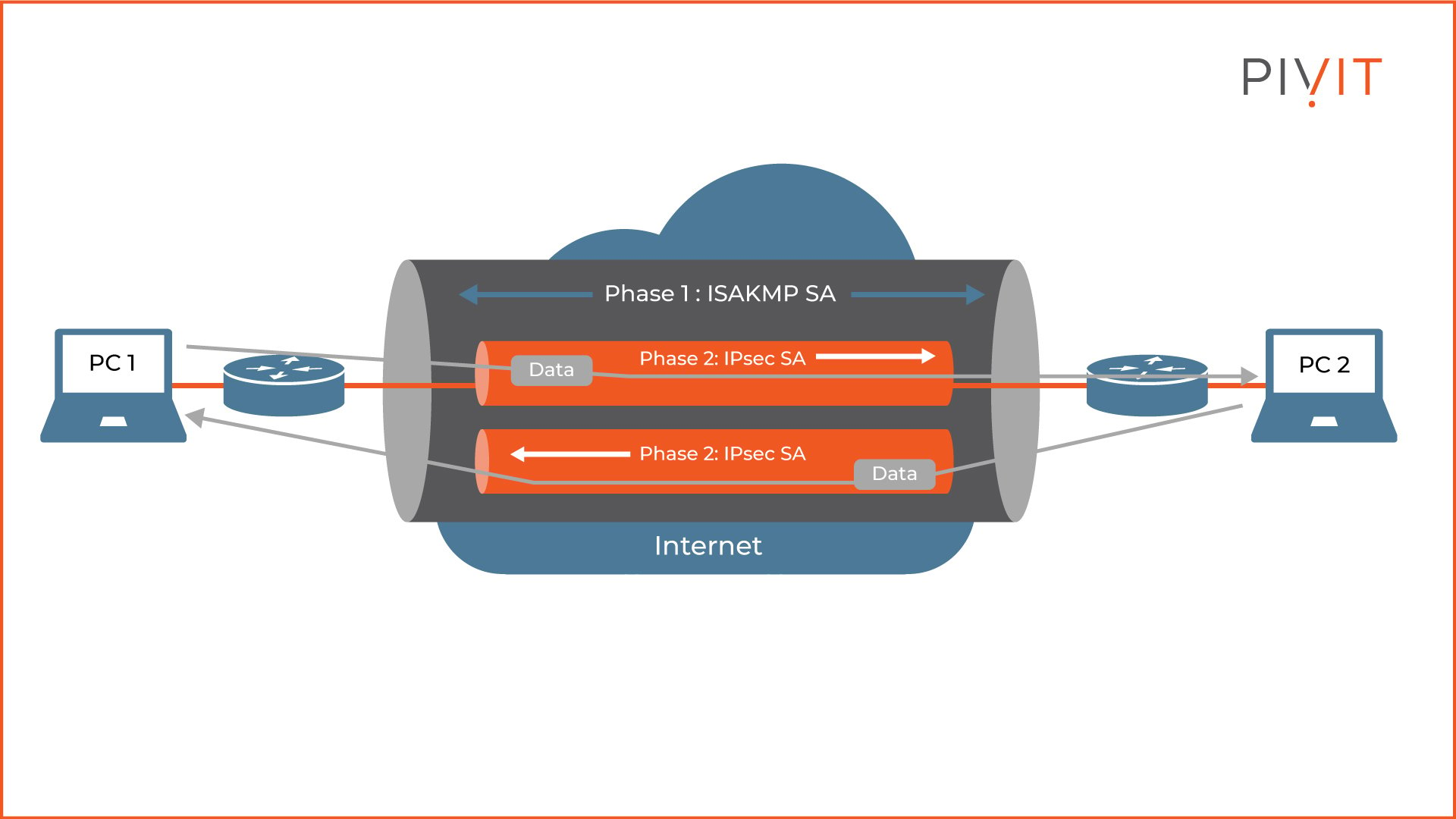
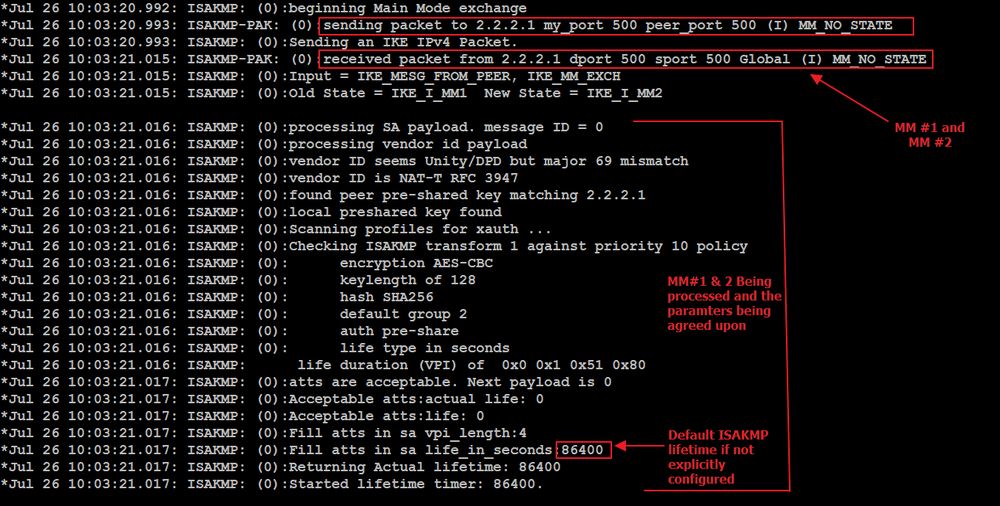
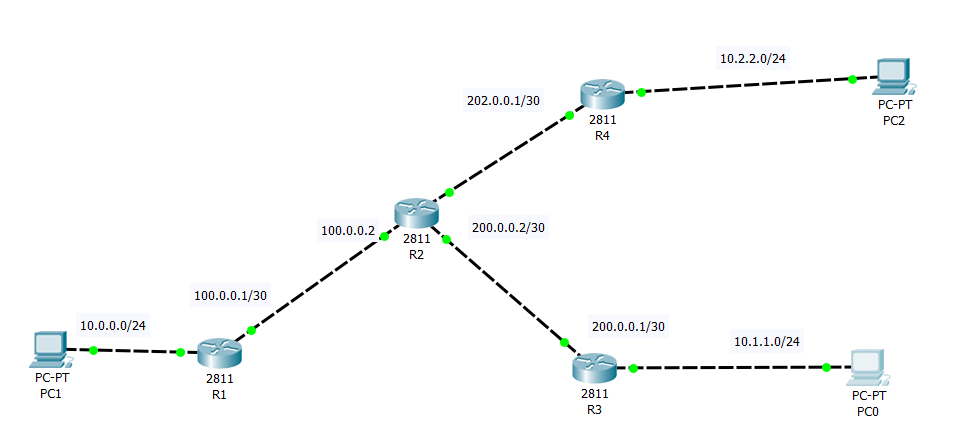
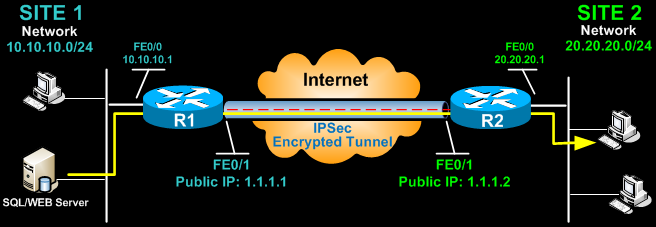
![Cisco 1800 Series Integrated Services Routers (Fixed) Software Configuration Guide - Configuring a VPN Using Easy VPN and an IPSec Tunnel [ Cisco 1800 Series Integrated Services Routers] - Cisco Cisco 1800 Series Integrated Services Routers (Fixed) Software Configuration Guide - Configuring a VPN Using Easy VPN and an IPSec Tunnel [ Cisco 1800 Series Integrated Services Routers] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/100001-200000/120001-130000/121001-122000/121782.ps/_jcr_content/renditions/121782.jpg)
Cisco 1800 Series Integrated Services Routers (Fixed) Software Configuration Guide - Configuring a VPN Using Easy VPN and an IPSec Tunnel [ Cisco 1800 Series Integrated Services Routers] - Cisco
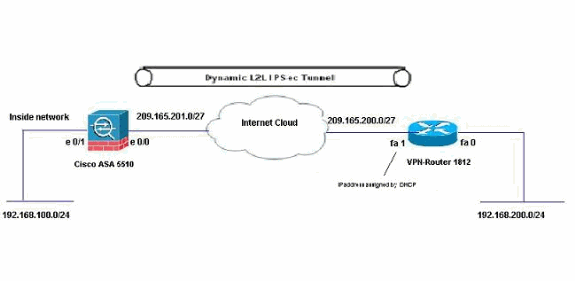
Dynamic IPsec Tunnel Between a Statically Addressed ASA and a Dynamically Addressed Cisco IOS Router that uses CCP Configuration Example - Cisco